
The majority of businesses are now shifting to digital platforms to take advantage of technological advancements and expand their reach and efficiency. Enterprises can manage and grow their businesses more effectively thanks to the cloud’s ability to interact with numerous networks regularly. But several cloud-based cybersecurity issues need a cloud-based system to be safe.
There are now Cloud Security Posture Management (CSPM) tools available on the market for identifying compliance issues in the cloud architecture. CSPM products, their features, relevance, and considerations for purchasing IT security technologies for the enterprise will be discussed here. The top CSPM tools on the market have also been selected for your company’s benefit.
Here is our list of the best Cloud Workload Security Platforms (CWSP) tools:
- ManageEngine Application Manager EDITOR’S CHOICE The tool stands out for its deep diagnostics and AI-powered insights that help IT/DevOps teams manage and monitor cloud security issues. Download a 30-day free trial.
- CrowdStrike Horizon – Offers constant monitoring and secure cloud deployment with enhanced efficiency.
- CloudGuard’s Posture Management – Excels in multi-cloud asset management and compliance adherence.
- Lacework – Distinguishes itself with data-driven security and automated cloud compliance features.
- Fugue – Ensures secure cloud development with its uniform policy engine and extensive visualization capabilities.
- Threat Stack – Provides integrated observability and robust AWS monitoring for enhanced cloud security.
- Trend Micro Hybrid Cloud Security Solution – Focuses on cloud architects, offering automated detection and cloud environment protection.
- BMC Helix Cloud Security – Delivers simplified cloud security posture management and compliance with major standards.
What are Cloud Workload Security Platforms (CWSP)?
CWSP tools enable enterprises to identify and remediate security compliance issues via automated monitoring and assessments. They keep an eye out for both incorrectly implemented rules and incorrectly configured cloud apps, containers, infrastructure, and services. Anomalies and misconfigurations may be automatically fixed by CWSP tools, which are triggered by administrator-defined rules.
Security posture monitoring (CWSP) is the only tool that provides continuous monitoring and visibility of security posture across heterogeneous computing environments while providing automated detection and remediation of issues. CWSP tools are the only ones that can provide this level of automation across a wide range of platforms.
Why do we need Cloud Workload Security Platforms (CWSP)?
With the help of CWSP, one may protect the cloud environment and limit the risk of data breaches in a cloud environment.
Every day, a cloud makes connections to a variety of different networks. Cyberattacks are more likely as a result of this. As a result, cloud-based systems should be protected and secured by CWSP tools. Multi-cloud visibility is made possible by security technologies, which shield data from unintentional vulnerability or setup errors. It is also possible to scan and analyze the surroundings in real-time and find concealed risks. In addition, it reduces false positives, i.e., artificial intelligence’s alert fatigue.
Things to remember before choosing Cloud Workload Security Platforms (CWSP)
A CWSP tool must be chosen based on several factors:
- The company’s demand Evaluate your needs in light of the company’s priorities and identify the most pressing issues. Don’t rush into investing in new technology without thoroughly considering the security risks of your firm and the cloud environment. Go over a variety of options before deciding on the best one for your organization.
- Check out the Extraordinary Features Advanced features such as monitoring capabilities and automatic setups must be taken into account when selecting a solution for your firm.
- Price Information Keep in mind your spending limit at all times. Online, you’ll find a wide range of tools with a wide range of functions for a low price. An investment in an affordable tool with similar features is preferable to an investment in an expensive tool with the same features. Don’t rush into deciding before you’ve looked at the plans and price of all the options.
- Access to the Free Trial Session Many tools offer free trial features that include all of the resources needed to begin the task. It’s best to look for these tools and see if the members of the team think they’re adequate before starting the procedure. It can also help you evaluate the tool and switch if necessary.
The Best CWSP Tools
The following are some of the most common CWSP tools, which may be used by both small and large enterprises.
Our Methodology for Selecting the Best CWSP Tool:
We’ve broken down our analysis for you based on these key criteria:
- Depth and breadth of cloud security features.
- Ease of integration with existing IT/DevOps environments.
- Compliance with major industry standards and regulations.
- The efficiency of real-time monitoring and threat detection.
- User-friendliness and support for multiple cloud environments.
1. ManageEngine Applications Manager (FREE TRIAL)
ManageEngine Applications Manager is recognized as one of the top solutions for Cloud Security Posture Management (CSPM). The tool comes with various monitoring and management capabilities that enable team members to gain end-to-end performance visibility, identify compliance issues, and other security issues in real-time. You can even resolve performance issues across leading cloud service providers such as AWS, Azure, GCP, Oracle Cloud, and OpenStack.
Key Features
- Full-stack visibility
- AI-assisted smart alerts
- Automated discovery
- Customizable Dashboard
Why do we recommend it?
ManageEngine Applications Manager is best known among IT and DevOps teams for delivering unified visibility and performance troubleshooting solutions. With this tool in hand, team members can perform deep application diagnostics and manage different cloud service providers from a single console.
Some of the prominent characteristics include:
- A unified console that enables team members to monitor servers, applications, metrics, user experience, cloud environments, and more.
- Customizable dashboards with access to 500+ pre-built reports.
- Offers access to AI-assisted smart alerts for performance anomalies and critical issues
- Supports monitoring across 150+ technologies, including AWS, Azure, GCP, Oracle Cloud, OpenStack, containers (Docker, Kubernetes, OpenShift), and virtualization environments.
- Automatically detects applications, starts visualizing dependencies, and maps business services to identify the root cause of the problem.
- Generates ML-driven forecasting reports.
- Offers code-level visibility and request tracing.
ManageEngine Application Manager allows businesses to connect with a wide range of tools and services for better analysis and troubleshooting. It even offers flexible deployment options depending on your environment and needs. One can even customize a dashboard and display insightful reports in front to perform trend and capacity planning, SLA compliance tracking, or gain a better graphical view of data collected from multiple sources in real-time.
Who is it recommended for?
IT professionals and DevOps teams looking for an all-in-one monitoring solution for their applications, cloud services, and infrastructure must go with this tool.
Pros:
- Offers graphs for trend analysis and in-depth insight presentation.
- Provides full-stack visibility into private, public, and hybrid cloud resources.
- Comes with 500+ pre-built reports
- Notifies and alerts using different channels in real-time.
Cons:
- The wide range of features might be a bit too much for some users.
Buyers can opt for paid versions to monitor applications at a larger scale or try the 30-day free trial version with access to several advanced features and benefits. Get started with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Applications Manager is our editor’s choice for Cloud Workload Security Platforms (CWSP) tools because it comes with advanced monitoring capabilities. End-to-end visibility into the entire application stack and cloud resources makes it easier for business owners and IT professionals to detect issues in real-time and troubleshoot them faster. Thus, it reduces the chances of poor operations, downtime, or slowdowns. Further, having this tool in hand, users can track major cloud services like AWS, Microsoft Azure, and Google Cloud Platform, resulting in improved performance and efficiency. It is one of the versatile solutions that offers pre-built reports, tool integrations, AI-assisted smart alerts, and other functionalities, making it a top choice compared to other solutions.
Download: Download a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/applications_manager/
OS: Windows, Linux
2. CrowdStrike Horizon
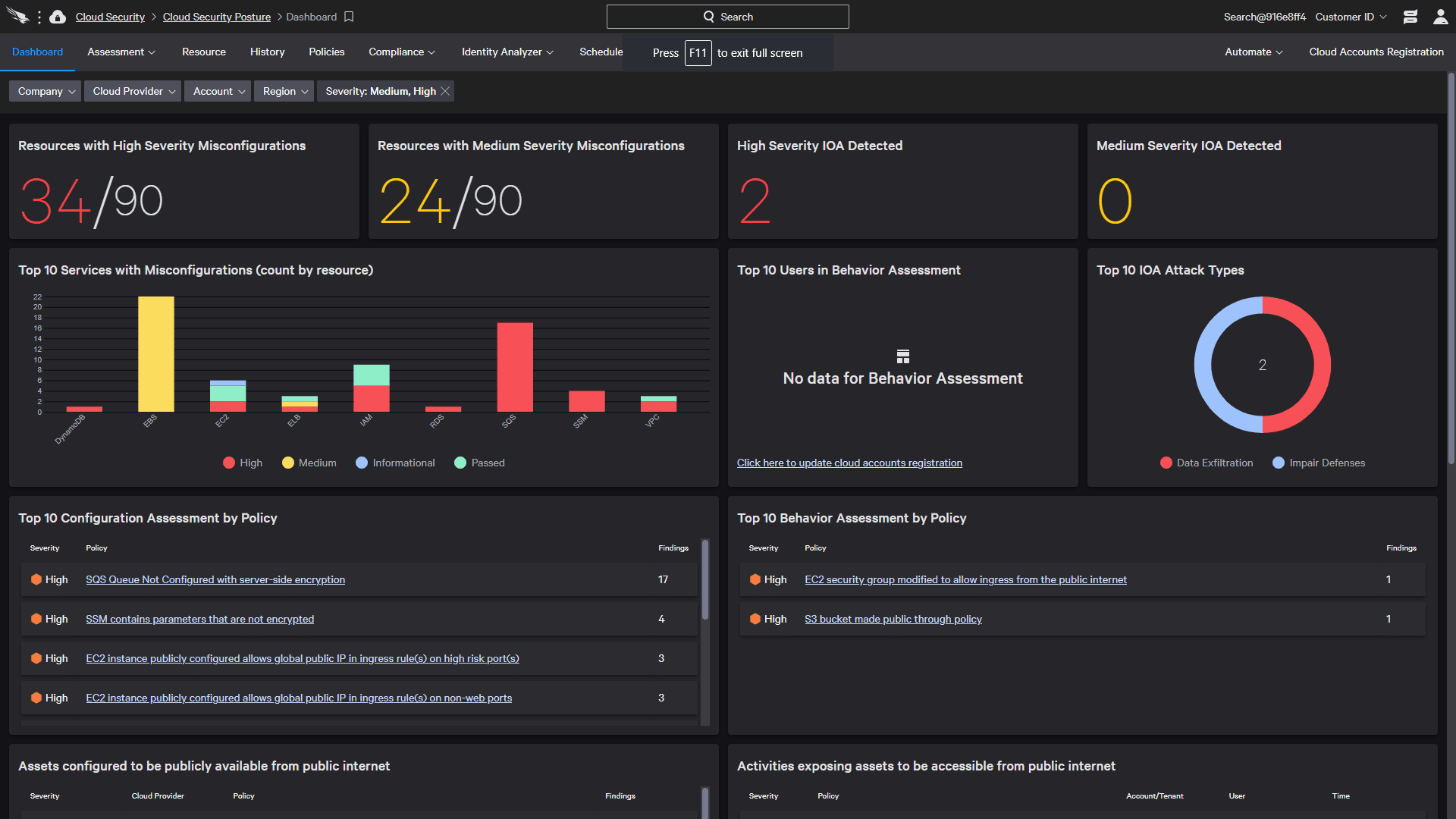
It’s an agentless cloud-native Defense that constantly checks your environment for errors. CrowdStrike Horizon Agentless helps to eliminate security omissions. CrowdStrike Falcon Horizon delivers a single source of truth for cloud resources, providing you a complete insight into a multi-cloud environment.
Key Features:
- Constant and intelligent monitoring of cloud resources to uncover errors and dangers before they become an issue.
- Secure cloud application deployment with greater speed and efficiency.
- Unified visibility and control across many cloud environments.
- Security problems are handled in a step-by-step manner.
- For developers, guardrails are a way to keep them from making expensive errors.
- Targeted threat detection is designed to minimize alarm fatigue.
- The integration with SIEM solutions is seamless.
Why do we recommend it?
CrowdStrike Horizon is recommended for its proactive approach in monitoring cloud resources and ensuring secure application deployment.
The facts and insights you get about your overall security posture are complemented by suggestions on how to prevent future security concerns.
Who is it recommended for?
This tool is suitable for businesses requiring comprehensive cloud security solutions, especially in multi-cloud environments.
Pros:
- Offers continuous monitoring of cloud resources.
- Enhances cloud application deployment security.
- Provides unified control across multiple cloud platforms.
Cons:
- May require a learning curve for full utilization.
Website link: https://www.crowdstrike.com/cloud-security-products/falcon-horizon-cspm/
3. CloudGuard’s Posture Management
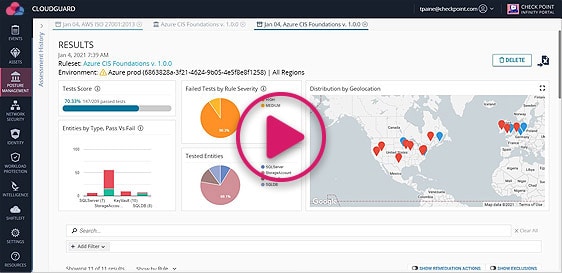
API-based agentless SaaS platform CloudGuard Posture Management optimizes administration across multi-cloud assets as part of the CloudGuard Cloud-Native Security Platform. Misconfiguration detection, security posture assessment, and visualization are some of the services provided, as are the implementation of security best practices and compliance frameworks.
Key Features:
- CloudGuard Posture Management enables users to apply gold standard criteria across projects, accounts, virtual networks, and geographies. Users may view their security posture and target, prioritize, and automatically fix problems.
- CloudGuard Posture Management ensures that users automatically adhere to regulatory requirements and security best practices. Users are constantly informed of their security and compliance status through comprehensive reporting.
- Privileged identity protection, based on Identity Access Management (IAM) roles and users, allows users to prevent unauthorized access to critical activities. CloudGuard Posture Management conducts frequent audits of IAM users and roles to look for anomalies.
Why do we recommend it?
CloudGuard’s Posture Management is favored for its effectiveness in optimizing cloud asset administration and enhancing security compliance.
Who is it recommended for?
It’s best for organizations managing diverse cloud assets and requiring stringent compliance and security measures.
Pros:
- Streamlines management across multi-cloud assets.
- Ensures adherence to regulatory and security standards.
- Offers privileged identity protection.
Cons:
- Complexity may be challenging for smaller teams.
Website link: https://www.checkpoint.com/cloudguard/cloud-security-posture-management/
4. Lacework
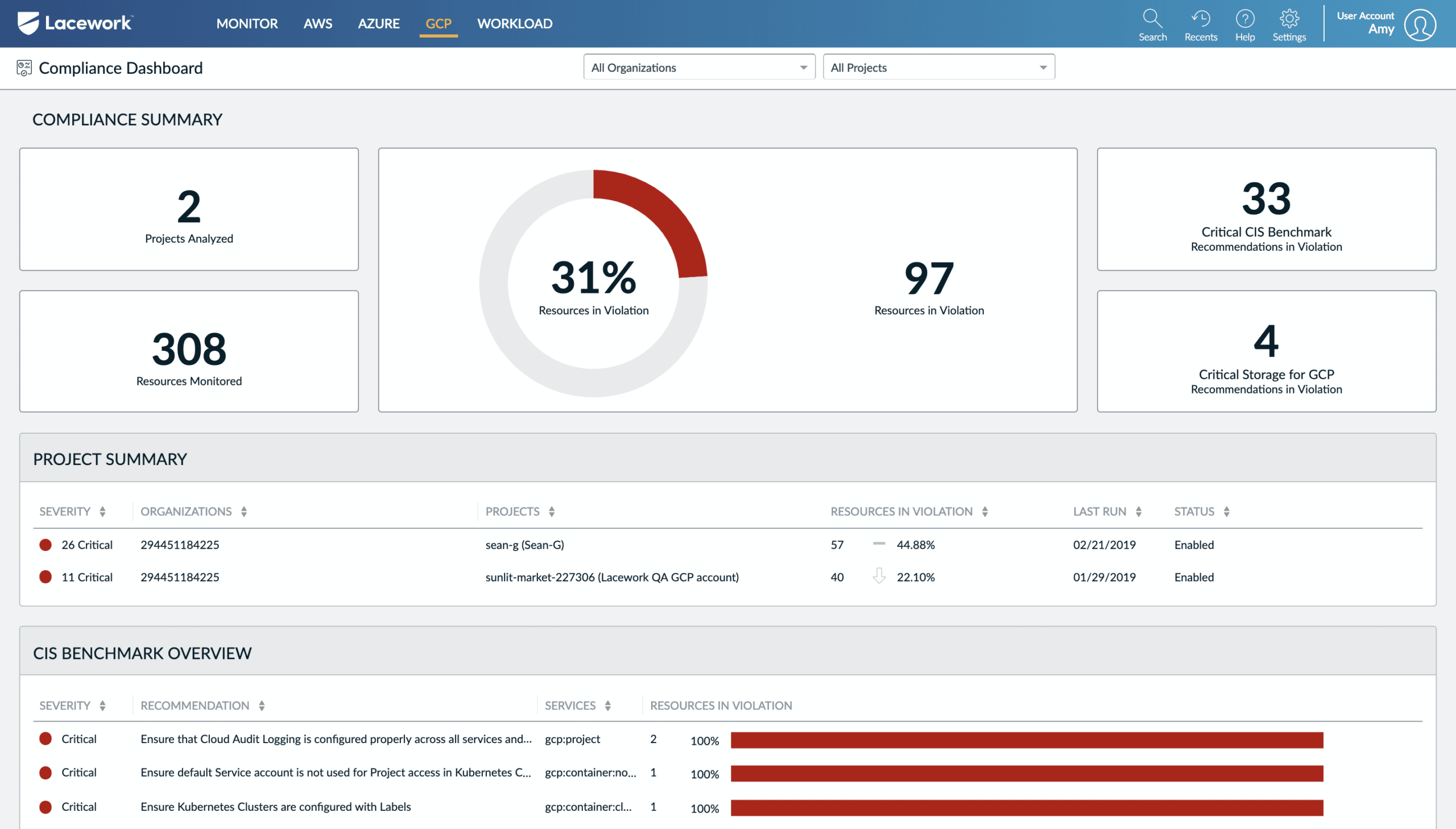
Data-driven cloud security platform Lacework automates cloud security at scale, enabling customers to innovate quickly and safely. Lacework gathers, analyses, and correlates data across an organization’s Kubernetes, AWS, Azure, and GCP systems with pinpoint precision, and then distills it down to a few important security events. Its automatic detection of intrusions, security visibility, one-click investigation, and easy cloud compliance sets Lacework apart from its rivals.
Key Features:
- Lacework alerts enterprises to any changes to rules, roles, or accounts, and notifies them of any new action. It does this by detecting new activity, documenting changes, and alerting users.
- Lacework discovers IAM issues, checks for logging best practices monitors essential account actions such as illegal API requests, and maintains safe network setups to ensure that users aren’t missing anything.
- Lacework users may maintain their compliance and security up to date with a daily re-audit. Unusual actions are accounted for in lacework analysis, regardless of whether they are legal or illegal.
Why do we recommend it?
Lacework is recommended for its data-driven approach to cloud security, enabling automation and precision in threat detection and compliance.
Who is it recommended for?
Ideal for organizations looking to automate their cloud security processes, especially in large-scale operations.
Pros:
- Provides automated, data-driven cloud security.
- Offers effective intrusion detection capabilities.
- Maintains up-to-date compliance.
Cons:
- May be more than required for smaller setups.
Website link: https://www.lacework.com/
5. Fugue

Security and compliance platform Fugue safeguards the whole development lifecycle with a uniform policy engine backed by the Open Policy Agent (OPA). Security and cloud engineering teams have greater confidence in cloud security because of Fugue, enabling them to operate more effectively and efficiently. Security checks on CloudFormation, AWS, Kubernetes manifests, and docker files can be performed using Fugue and actionable remedial feedback may be sent using developer-friendly interfaces.
Key Features:
- Open-source policy engine Fugue enables organizations to implement compliance and security policies across the software development lifecycle.
- Fugue’s resource data engine delivers extensive visualization and reporting capabilities by continually capturing snapshots of client cloud settings to record detailed cloud resource configurations, connections, characteristics, and drift.
- Fugue’s Regula policy engine lets clients safeguard their CloudFormation and Terraform IAC at every stage of development and deployment.
Why do we recommend it?
Fugue stands out for its powerful open-source policy engine and its ability to offer extensive visualization and reporting features.
Who is it recommended for?
Fugue is recommended for teams focusing on secure cloud development lifecycle management, particularly those using IAC tools.
Pros:
- Employs a robust open-source policy engine.
- Delivers comprehensive visualization of cloud settings.
- Protects Infrastructure as Code at all stages.
Cons:
- Might be complex for users new to policy engines.
Website link: https://www.fugue.co/
6. Threat Stack
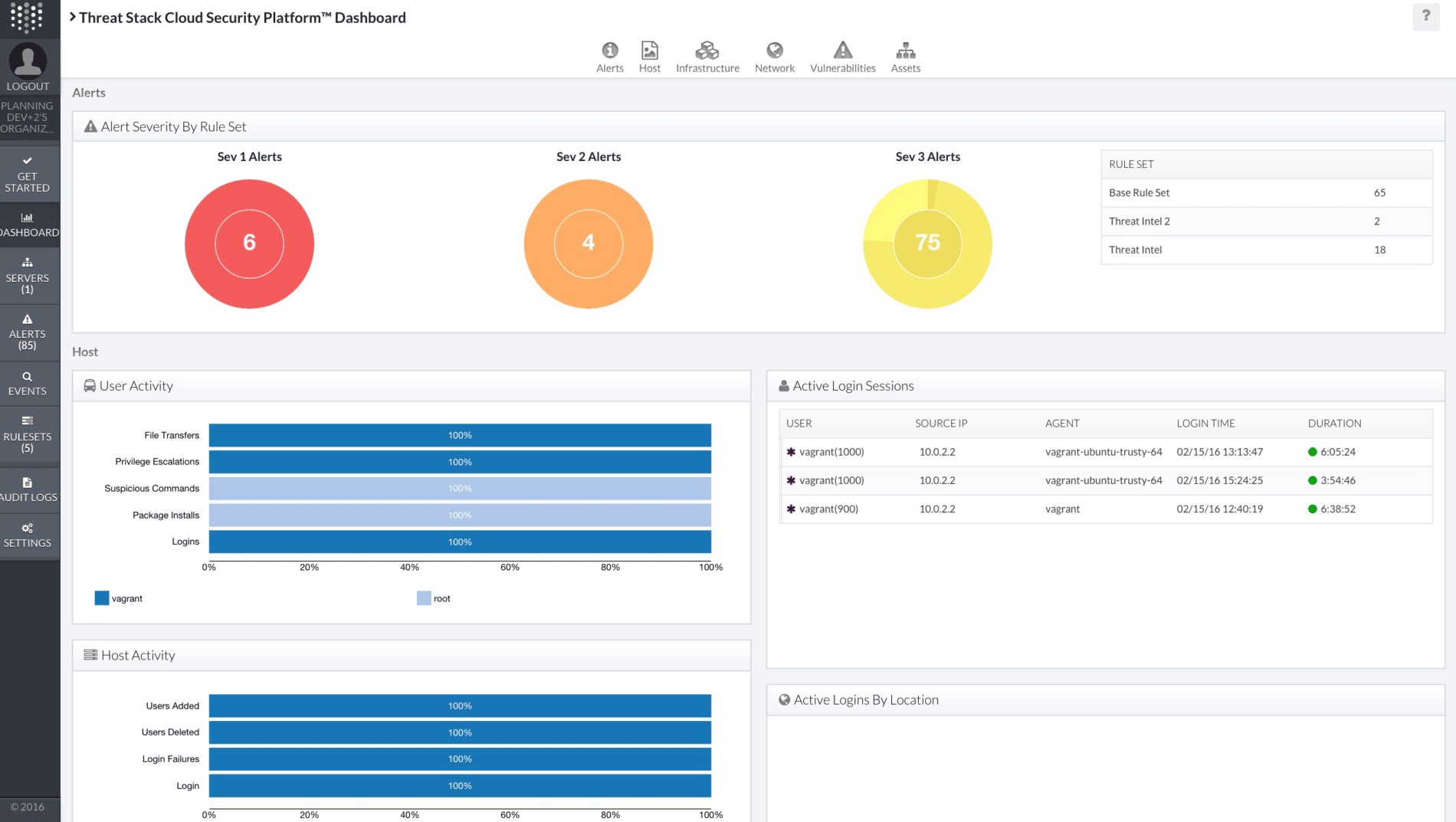
Through the integration of development, security, and operations in to a single, observable platform, Threat Stack Cloud Security Platform improves user productivity. Observability may be found in the cloud management dashboard, containers, hosts, orchestration, and serverless layers. Using Threat Stack, organizations can identify known threats at scale and immediately discover abnormalities in their computer systems.
Key Features:
- Threat Stack CWSP uses AWS CloudTrail data to notify customers of changes made, such as instances being created in unused regions.
- Threat Stack’s approach to IAM rules involves monitoring your AWS accounts to verify that users are adhering to the regulations, such as root access and password requirements.
- Visibility allows users to examine an inventory of servers and instances in many AWS accounts. They may also be able to view vital information such as the ID, IP, area, kind, and so on.
- Threat Stack gathers data from a wide range of AWS profiles by scanning setups across the major AWS services.
Why do we recommend it?
Threat Stack is notable for integrating development, security, and operations, providing thorough AWS monitoring and security.
Who is it recommended for?
This tool is ideal for organizations heavily using AWS services and seeking an integrated approach to cloud security.
Pros:
- Integrates development, security, and operational monitoring.
- Utilizes AWS CloudTrail for detailed monitoring.
- Scans a wide range of AWS setups for comprehensive coverage.
Cons:
- Focused mainly on AWS, less versatile for other platforms.
Website link: https://www.threatstack.com/
7. Trend Micro Hybrid Cloud Security Solution

Security for cloud architects is the focus of the Trend Micro Hybrid Cloud Security Solution. With this solution, customers can easily protect their cloud infrastructure with a single, integrated platform. Because of the cloud’s security, clients may take advantage of its advantages and efficiency. It’s not only cloud platforms that Trend Micro Hybrid supports, but also DevOps processes and toolchains.
Key Features:
- While covering the network layer, Trend Micro Hybrid Cloud automates the detection and protection of cloud environments and provides easy and scalable cloud security throughout migration and growth.
- Security for your cloud services is made easier with Trend Micro Cloud One’s application-aware protection that keeps up with the latest development methodologies and technologies.
Why do we recommend it?
Trend Micro Hybrid Cloud Security Solution is recommended for its ability to automate protection in cloud environments and support various development methodologies.
Who is it recommended for?
It’s best suited for cloud architects and DevOps teams needing a solution that evolves with their cloud infrastructure and processes.
Pros:
- Automates detection and protection in cloud environments.
- Compatible with various development methodologies.
- Offers scalable solutions for growing infrastructures.
Cons:
- May require advanced understanding for full functionality.
Website link: https://www.trendmicro.com/en_us/business/products/hybrid-cloud.html
8. BMC Helix Cloud Security

Using BMC Helix Cloud Security, services like Infrastructure as a Service (IaaS) and Platform as Service (PaaS) can be set up securely and consistently, with an audit trail, without the need for any scripting. Improved control and reduced risk are achieved by integrating compliance and security testing into the service delivery and cloud operations of BMC Helix Cloud Security.
Key Features:
- BMC Helix Cloud Security simplifies the administration of cloud security posture for customers that utilize Center for Internet Security (CIS) rules for cloud assets.
- The software’s self-driving remediation, automated remediation through an intuitive user interface, and customized remediation assistance all simplify the repair process for end-users. users.
- CIS, GDPR, and PCI are just a few of the regulations that BMC Helix Cloud Security adheres to. BMC Helix also supports the creation of custom policies.
Why do we recommend it?
BMC Helix Cloud Security is recommended for its simplified approach to managing cloud security posture and its automated compliance features.
Who is it recommended for?
This tool is ideal for organizations requiring consistent and secure setup of cloud services, with a focus on compliance and policy management.
Pros:
- Simplifies management of cloud security posture.
- Integrates automated compliance and security testing.
- Allows for custom policy creation.
Cons:
- May be more than necessary for smaller cloud setups.
Website link: https://www.bmc.com/it-solutions/bmc-helix-cloud-security.html
Conclusion
CWSP is a robust set of tools for securing your cloud data and identifying and resolving problems in various cloud infrastructures due to incorrect configuration. As more and more individuals migrate to the cloud, the need for effective security technologies has grown.
This is where CWSP tools are put to use. Compliant risk detection, risk visualization, and risk assessment capabilities are all provided by these software applications. In addition, they provide alert systems that keep cloud customers up to date on attacks and other security concerns they may be exposed to.
With these tools, administrators can execute instance scanning for misconfigurations, maintain consistency across all cloud environments, monitor storage buckets, and conduct risk assessments.



